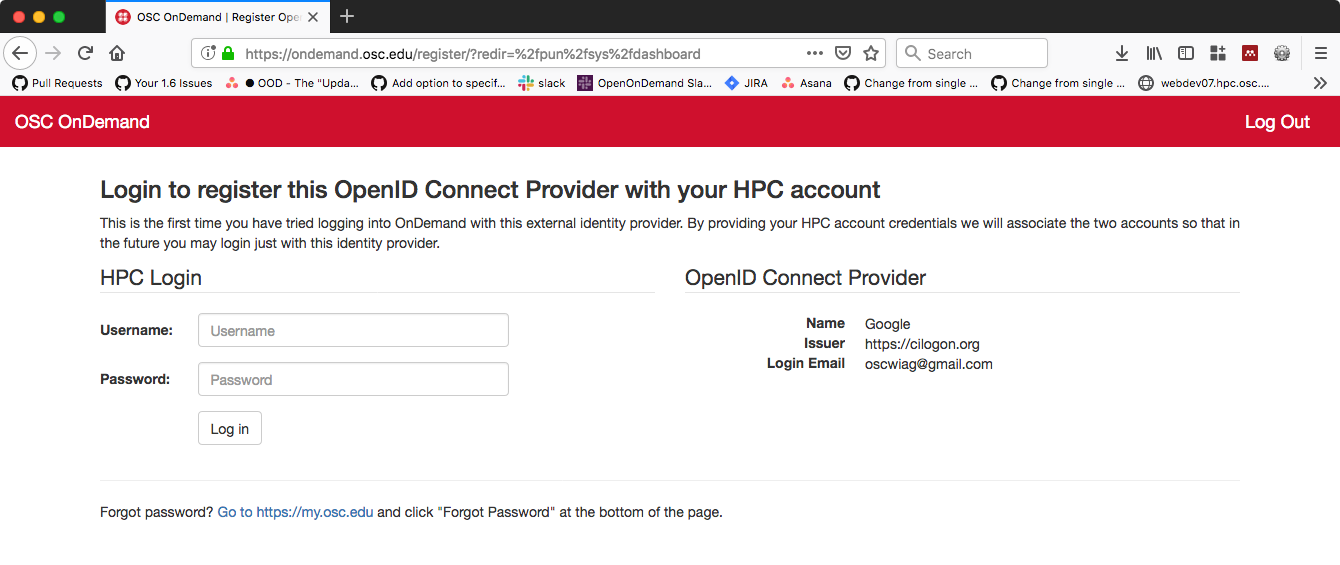
@m_ludwig For OSC the Keycloak login page is a split view using a custom theme [1]. The left side is Keycloak login that is backed by LDAP. The right side is Identity Provider of CILogon [2]. The “firstBrokerLoginFlowAlias” of “browser” basically redirects new users using CILogon to just Keycloak login page that upon successful login will map their CILogon identity to their LDAP record in Keycloak. Subsequent logins with that CILogon provider will redirect to OnDemand rather than require a second authentication to perform the mapping.
The only issue we’ve had is if you login with something like OSU via CILogon then log in with Google, that will cause duplicate record errors in Keycloak due to how the database schema is setup. The CILogon claim ID changes based on the provider used and Keycloak expects Identity Providers to always return the same claim ID for a given user. The user account portal for Keycloak allows users to remove their mapping and so we’ve just overloaded a help link in OnDemand to allow direct users to the page in Keycloak that allows them to delete their CILogon mapping. I think I also had to avoid the “email” value in “defaultScope” to prevent Keycloak trying to automatically create users inside Keycloak.
If you support a “Social” Identity Provider in Keycloak like CILogon the you can custom the flow via “firstBrokerLoginFlowAlias” to redirect users to registration pages or other parts of Keycloak. The flow aspect of Keycloak is highly configurable.
The self-registration at OSC is handled by a different application that ultimately writes records to LDAP. The LDAP configuration for Keycloak is set to read-only.
[1] : https://github.com/OSC/keycloak-theme
[2]:
[ {
"alias" : "cilogon",
"displayName" : "CILogon",
"internalId" : "cilogon-osc",
"providerId" : "oidc",
"enabled" : true,
"updateProfileFirstLoginMode" : "on",
"trustEmail" : false,
"storeToken" : false,
"addReadTokenRoleOnCreate" : false,
"authenticateByDefault" : false,
"linkOnly" : false,
"firstBrokerLoginFlowAlias" : "browser",
"config" : {
"hideOnLoginPage" : "false",
"userInfoUrl" : "https://cilogon.org/oauth2/userinfo",
"validateSignature" : "false",
"clientId" : "<OMIT>",
"tokenUrl" : "https://cilogon.org/oauth2/token",
"uiLocales" : "false",
"backchannelSupported" : "false",
"useJwksUrl" : "true",
"loginHint" : "false",
"authorizationUrl" : "https://cilogon.org/authorize",
"disableUserInfo" : "false",
"clientSecret" : "**********",
"defaultScope" : "openid profile org.cilogon.userinfo"
}
} ]
 I’m curious to learn more about how other HPC sites are approaching this.
I’m curious to learn more about how other HPC sites are approaching this.